Quantum Information And Computation
Quantum Information And Computation
Paper 4, Section I, 10D
Part II, 2018Let denote the set of all -bit strings. Suppose we are given a 2-qubit quantum gate which is promised to be of the form
but the 2-bit string is unknown to us. We wish to determine with the least number of queries to . Define , where is the identity operator and .
(a) Is unitary? Justify your answer.
(b) Compute the action of on , and the action of on , in each case expressing your answer in terms of and . Hence or otherwise show that may be determined with certainty using only one application of the gate , together with any other gates that are independent of .
(c) Let be the function having value 0 for all and having value 1 for . It is known that a single use of can be implemented with a single query to a quantum oracle for the function . But suppose instead that we have a classical oracle for , i.e. a black box which, on input , outputs the value of . Can we determine with certainty using a single query to the classical oracle? Justify your answer.
Paper 3, Section I, 10D
Part II, 2018Let denote the set of all -bit strings. For any Boolean function on 2 bits consider the linear operation on 3 qubits defined by
for all and denoting addition of bits modulo 2 . Here the first register is a 2-qubit register and the second is a 1-qubit register. We are able to apply only the 1-qubit Pauli and Hadamard gates to any desired qubits, as well as the 3 -qubit gate to any three qubits. We can also perform measurements in the computational basis.
(a) Describe how we can construct the state
starting from the standard 3-qubit state .
(b) Suppose now that the gate is given to us but is not specified. However is promised to be one of two following cases:
(i) is a constant function (i.e. for all , or for all ),
(ii) for any 2-bit string we have (with as above).
Show how we may determine with certainty which of the two cases (i) or (ii) applies, using only a single application of .
Paper 2, Section I,
Part II, 2018(a) The classical controlled- operation applied to the 2-bit string (for or 1 ) achieves the cloning of , i.e. the result is . Let denote the quantum controlled (or controlled-NOT) operation on two qubits. For which qubit states will the application of to (with the first qubit being the control qubit) achieve the cloning of ? Justify your answer.
(b) Let and be two distinct non-orthogonal quantum states. State and prove the quantum no-cloning theorem for unitary processes.
Paper 1, Section I, D
Part II, 2018(a) Define what it means for a 2-qubit state of a composite quantum system to be entangled.
Consider the 2-qubit state
where is the Hadamard gate. From the definition of entanglement, show that is an entangled state.
(b) Alice and Bob are distantly separated in space. Initially they each hold one qubit of the 2-qubit entangled state
They are able to perform local quantum operations (unitary gates and measurements) on quantum systems they hold. Alice wants to communicate two classical bits of information to Bob. Explain how she can achieve this (within their restricted operational resources) by sending him a single qubit.
Paper 2, Section II, D
Part II, 2018(a) Suppose that Alice and Bob are distantly separated in space and each has one qubit of the 2-qubit state . They also have the ability to perform local unitary quantum operations and local computational basis measurements, and to communicate only classically. Alice has a 1-qubit state (whose identity is unknown to her) which she wants to communicate to Bob. Show how this can be achieved using only the operational resources, listed above, that they have available.
Suppose now that a third party, called Charlie, joins Alice and Bob. They are all mutually distantly separated in space and each holds one qubit of the 3-qubit state
As previously with Alice and Bob, they are able to communicate with each other only classically, e.g. by telephone, and they can each also perform only local unitary operations and local computational basis measurements. Alice and Bob phone Charlie to say that they want to do some quantum teleportation and they need a shared state (as defined above). Show how Charlie can grant them their wish (with certainty), given their joint possession of and using only their allowed operational resources. [Hint: It may be useful to consider application of an appropriate Hadamard gate action.]
(b) State the quantum no-signalling principle for a bipartite state of the composite system .
Suppose we are given an unknown one of the two states
and we wish to identify which state we have. Show that the minimum error probability for this state discrimination task is zero.
Suppose now that we have access only to qubit of the received state. Show that we can now do no better in the state discrimination task than just making a random guess as to which state we have.
Paper 3, Section II,
Part II, 2018In this question you may assume the following fact about the quantum Fourier transform if and , where , then
where .
(a) Let denote the integers modulo . Let be a periodic function with period and with the property that is one-to-one within each period. We have one instance of the quantum state
and the ability to calculate the function on at most two values of our choice.
Describe a procedure that may be used to determine the period with success probability . As a further requirement, at the end of the procedure we should know if it has been successful, or not, in outputting the correct period value. [You may assume that the number of integers less than that are coprime to is .
(b) Consider the function defined by .
(i) Show that is periodic and find the period.
(ii) Suppose we are given the state and we measure the second register. What are the possible resulting measurement values and their probabilities?
(iii) Suppose the measurement result was . Find the resulting state of the first register after the measurement.
(iv) Suppose we measure the state (with from part (iii)). What is the probability of each outcome ?
Paper 4, Section I,
Part II, 2019(a) Define the order of for coprime integers and with . Explain briefly how knowledge of this order can be used to provide a factor of , stating conditions on and its order that must be satisfied.
(b) Shor's algorithm for factoring starts by choosing coprime. Describe the subsequent steps of a single run of Shor's algorithm that computes the order of mod with probability .
[Any significant theorems that you invoke to justify the algorithm should be clearly stated (but proofs are not required). In addition you may use without proof the following two technical results.
Theorem : For positive integers and with , and any , let be the largest integer such that Let QFT denote the quantum Fourier transform . Suppose we measure to obtain an integer with Then with probability will be an integer closest to a multiple of for which the value of (between 0 and ) is coprime to .
Theorem CF: For any rational number with and with integers a and having at most digits each, let with and coprime, be any rational number satisfying
Then is one of the convergents of the continued fraction of and all the convergents can be classically computed from in time .]
Paper 3, Section I,
Part II, 2019Let denote the set of all -bit strings and write . Let denote the identity operator on qubits and for introduce the -qubit operator
where is the Hadamard operation on each of the qubits, and and are given by
Also introduce the states
Let denote the real span of and .
(a) Show that maps to itself, and derive a geometrical interpretation of the action of on , stating clearly any results from Euclidean geometry that you use.
(b) Let be the Boolean function such that iff . Suppose that . Show that we can obtain an with certainty by using just one application of the standard quantum oracle for (together with other operations that are independent of ).
Paper 2, Section I,
Part II, 2019The BB84 quantum key distribution protocol begins with Alice choosing two uniformly random bit strings and .
(a) In terms of these strings, describe Alice's process of conjugate coding for the BB84 protocol.
(b) Suppose Alice and Bob are distantly separated in space and have available a noiseless quantum channel on which there is no eavesdropping. They can also communicate classically publicly. For this idealised situation, describe the steps of the BB84 protocol that results in Alice and Bob sharing a secret key of expected length .
(c) Suppose now that an eavesdropper Eve taps into the channel and carries out the following action on each passing qubit. With probability , Eve lets it pass undisturbed, and with probability she chooses a bit uniformly at random and measures the qubit in basis where and . After measurement Eve sends the post-measurement state on to Bob. Calculate the bit error rate for Alice and Bob's final key in part (b) that results from Eve's action.
Paper 1, Section I, Introduce the 2 -qubit states
Part II, 2019where and are the standard qubit Pauli operations and .
(a) For any 1-qubit state show that the 3 -qubit state of system can be expressed as
where the 1 -qubit states are uniquely determined. Show that .
(b) In addition to you may now assume that . Alice and Bob are separated distantly in space and share a state with and labelling qubits held by Alice and Bob respectively. Alice also has a qubit in state whose identity is unknown to her. Using the results of part (a) show how she can transfer the state of to Bob using only local operations and classical communication, i.e. the sending of quantum states across space is not allowed.
(c) Suppose that in part (b), while sharing the state, Alice and Bob are also unable to engage in any classical communication, i.e. they are able only to perform local operations. Can Alice now, perhaps by a modified process, transfer the state of to Bob? Give a reason for your answer.
Paper 3, Section II, D
Part II, 2019Let denote a -dimensional state space with orthonormal basis . For any let be the operator on defined by
for all and .
(a) Define , the quantum Fourier transform (for any chosen .
(b) Let on (for any chosen ) denote the operator defined by
for . Show that the Fourier basis states for are eigenstates of . By expressing in terms of find a basis of eigenstates of and determine the corresponding eigenvalues.
(c) Consider the following oracle promise problem:
Input: an oracle for a function .
Promise: has the form where and are unknown coefficients (and with all arithmetic being .
Problem: Determine with certainty.
Can this problem be solved by a single query to a classical oracle for (and possible further processing independent of ? Give a reason for your answer.
Using the results of part (b) or otherwise, give a quantum algorithm for this problem that makes just one query to the quantum oracle for .
(d) For any , let and (all arithmetic being ). Show how and can each be implemented with one use of together with other unitary gates that are independent of .
(e) Consider now the oracle problem of the form in part (c) except that now is a quadratic function with unknown coefficients (and all arithmetic being mod 3), and the problem is to determine the coefficient with certainty. Using the results of part (d) or otherwise, give a quantum algorithm for this problem that makes just two queries to the quantum oracle for .
Paper 2, Section II, D
Part II, 2019Let be two quantum states and let and be associated probabilities with and . Alice chooses state with probability and sends it to Bob. Upon receiving it, Bob performs a 2-outcome measurement with outcomes labelled 0 and 1 , in an attempt to identify which state Alice sent.
(a) By using the extremal property of eigenvalues, or otherwise, show that the operator has exactly two nonzero eigenvalues, one of which is positive and the other negative.
(b) Let denote the probability that Bob correctly identifies Alice's sent state. If the measurement comprises orthogonal projectors (corresponding to outcomes 0 and 1 respectively) give an expression for in terms of and .
(c) Show that the optimal success probability , i.e. the maximum attainable value of , is
where .
(d) Suppose we now place the following extra requirement on Bob's discrimination process: whenever Bob obtains output 0 then the state sent by Alice was definitely . Show that Bob's now satisfies .
Paper 1, Section I, 10C
Part II, 2020Suppose we measure an observable on a qubit, where is a unit vector and is the vector of Pauli operators.
(i) Express as a matrix in terms of the components of .
(ii) Representing in terms of spherical polar coordinates as , rewrite the above matrix in terms of the angles and .
(iii) What are the possible outcomes of the above measurement?
(iv) Suppose the qubit is initially in a state . What is the probability of getting an outcome 1?
(v) Consider the three-qubit state
Suppose the second qubit is measured relative to the computational basis. What is the probability of getting an outcome 1? State the rule that you are using.
Paper 2, Section I, 10C
Part II, 2020Consider the set of states
where and (addition modulo 2 ).
(i) Show that
where denotes the Hadamard gate and CX denotes the controlled- gate.
(ii) Show that for any ,
[Hint: For any unitary operator , we have , where denotes the transpose of with respect to the computational basis.]
(iii) Suppose Alice and Bob initially share the state . Show using (*) how Alice can communicate two classical bits to Bob by sending him only a single qubit.
Paper 3, Section I,
Part II, 2020For and consider the operator
Let be a unitary operator on with action on given as follows
where is a constant in and are orthonormal states.
(i) Give an explicit expression of the state .
(ii) Find a for which .
(iii) Choosing in equation ( , calculate the state . For what choice of is this state proportional to ?
(iv) Describe how the above considerations can be used to find a marked element in a list of four items . Assume that you have the state and can act on it with a unitary operator that prepares the uniform superposition of four orthonormal basis states of . [You may use the operators (defined in (†)), and for any choice of and any .]
Paper 4, Section I, C
Part II, 2020(i) What is the action of on a state , where and denotes the Quantum Fourier Transform modulo ?
(ii) For the case write respectively in binary as thereby identifying the four-dimensional space as that of two qubits. Show that is an unentangled state of the two qubits.
(iii) Prove that , where .
[Hint: For if is not a multiple of .]
(iv) What is the action of on a state , for any ? Use the above to determine what the eigenvalues of are.
Paper 2, Section II, 15C
Part II, 2020(a) Show how the -qubit state
can be generated from a computational basis state of by the action of Hadamard gates.
(b) Prove that , where denotes the controlled- gate. Justify (without any explicit calculations) the following identity:
(c) Consider the following two-qubit circuit:
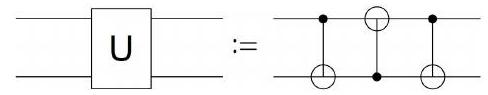
What is its action on an arbitrary 2-qubit state In particular, for two given states and , find the states and such that
(d) Consider the following quantum circuit diagram
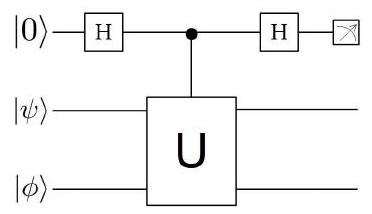
where the measurement is relative to the computational basis and is the quantum gate from part (c). Note that the second gate in the circuit performs the following controlled operation:
(i) Give expressions for the joint state of the three qubits after the action of the first Hadamard gate; after the action of the quantum gate ; and after the action of the second Hadamard gate.
(ii) Compute the probabilities and of getting outcome 0 and 1 , respectively, in the measurement.
(iii) How can the above circuit be used to determine (with high probability) whether the two states and are identical or not? [Assume that you are given arbitrarily many copies of the three input states and that the quantum circuit can be used arbitrarily many times.]
Paper 3, Section II, C
Part II, 2020Consider the quantum oracle for a function which acts on the state of qubits as follows:
The function is promised to have the following property: there exists a such that for any ,
where .
(a) What is the nature of the function for the case in which , and for the case in which ?
(b) Suppose initially each of the qubits are in the state . They are then subject to the following operations:
Each of the first qubits forming an input register are acted on by Hadamard gates;
The qubits are then acted on by the quantum oracle ;
Next, the qubits in the input register are individually acted on by Hadamard gates.
(i) List the states of the qubits after each of the above operations; the expression for the final state should involve the -bit "dot product" which is defined as follows:
where with and .
(ii) Justify that if then for any and any , , the following identity holds:
(iii) For the case , what is the probability that a measurement of the input register, relative to the computational basis of results in a string ?
(iv) For the case , show that the probability that the above-mentioned measurement of the input register results in a string , is equal to the following:
zero for all strings satisfying , and for any fixed string satisfying .
[State any identity you may employ. You may use .]
Paper 1, Section I,
Part II, 2021Alice wishes to communicate to Bob a 1-bit message or chosen by her with equal prior probabilities . For (respectively ) she sends Bob the quantum state (respectively ). On receiving the state, Bob applies quantum operations to it, to try to determine Alice's message. The Helstrom-Holevo theorem asserts that the probability for Bob to correctly determine Alice's message is bounded by , where , and that this bound is achievable.
(a) Suppose that and , and that Bob measures the received state in the basis , where and , to produce his output 0 or 1 , respectively. Calculate the probability that Bob correctly determines Alice's message, and show that the maximum value of over choices of achieves the Helstrom-Holevo bound.
(b) State the no-cloning theorem as it applies to unitary processes and a set of two non-orthogonal states . Show that the Helstrom-Holevo theorem implies the validity of the no-cloning theorem in this situation.
Paper 2, Section I, 10D
Part II, 2021Let denote the set of all -bit strings and let be a Boolean function which obeys either
(I) for all , or
(II) for exactly half of all .
Suppose we are given the -qubit state
Show how we may determine with certainty whether is of case (I) or case (II).
Suppose now that Alice and Bob are separated in space. Alice possesses a quantum oracle for a Boolean function and Bob similarly possess a quantum oracle for a Boolean function . These functions are arbitrary, except that either
(1) for all , or
(2) for exactly half of all .
Alice and Bob each have available a supply of qubits in state and each can apply local quantum operations (including their own function oracle) to any qubits in their possession. Additionally, they can send qubits to each other.
Show how Bob may decide with certainty which case applies, after he has received qubits from Alice. [Hint: You may find it helpful to consider the function , where denotes addition mod 2.]
Paper 3 , Section I, D
Part II, 2021Let be the joint state of a bipartite system with subsystems and separated in space. Suppose that Alice and Bob have access only to subsystems and respectively, on which they can perform local quantum operations.
Alice performs a unitary operation on and then a (generally incomplete) measurement on , with projectors labelled by her possible measurement outcomes . Then Bob performs a complete measurement on relative to the orthonormal basis labelled by his possible outcomes .
Show that the probability distribution of Bob's measurement outcomes is unaffected by whether or not Alice actually performs the local operations on described above.
Paper 4, Section I,
Part II, 2021Let be a state space of dimension with standard orthonormal basis labelled by . Let QFT denote the quantum Fourier transform and let denote the operation defined by .
(a) Introduce the basis defined by . Show that each is an eigenstate of and determine the corresponding eigenvalue.
(b) By expressing a generic state in the basis, show that QFT and QFT have the same output distribution if measured in the standard basis.
(c) Let be positive integers with , and let be an integer with . Suppose that we are given the state
where and are unknown to us. Using part (b) or otherwise, show that a standard basis measurement on QFT has an output distribution that is independent of .
Paper 2, Section II, D
Part II, 2021Alice and Bob are separated in space and can communicate only over a noiseless public classical channel, i.e. they can exchange bit string messages perfectly, but the messages can be read by anyone. An eavesdropper Eve constantly monitors the channel, but cannot alter any passing messages. Alice wishes to communicate an -bit string message to Bob whilst keeping it secret from Eve.
(a) Explain how Alice can do this by the one-time pad method, specifying clearly any additional resource that Alice and Bob need. Explain why in this method, Alice's message does, in fact, remain secure against eavesdropping.
(b) Suppose now that Alice and Bob do not possess the additional resource needed in part (a) for the one-time pad, but that they instead possess pairs of qubits, where , with each pair being in the state
where the real parameters are known to Alice and Bob and obey and . For each qubit pair in state , Alice possesses qubit and Bob possesses qubit . They each also have available a supply of ancilla qubits, each in state , and they can each perform local quantum operations on qubits in their possession.
Show how Alice, using only local quantum operations, can convert each state into by a process that succeeds with non-zero probability. [Hint: It may be useful for Alice to start by adjoining an ancilla qubit and work locally on her two qubits in
Hence, or otherwise, show how Alice can communicate a bit string of expected length to Bob in a way that keeps it secure against eavesdropping by Eve.
Paper 3, Section II, D
Part II, 2021Let denote the set of all -bit strings and let denote the space of qubits.
(a) Suppose has the property that for a unique and suppose we have a quantum oracle .
(i) Let and introduce the operators
on , where is the identity operator. Give a geometrical description of the actions of and on the 2-dimensional subspace of given by the real span of and . [You may assume without proof that the product of two reflections in is a rotation through twice the angle between the mirror lines.]
(ii) Using the results of part (i), or otherwise, show how we may determine with certainty, starting with a supply of qubits each in state and using only once, together with other quantum operations that are independent of .
(b) Suppose , where is a fixed linear subspace with orthogonal complement . Let denote the projection operator onto and let , where is the identity operator on .
(i) Show that any can be written as , where , and and are normalised.
(ii) Let and . Show that .
(iii) Now assume, in addition, that and that for some unitary operation . Suppose we can implement the operators as well as the operation . In the case , show how the -qubit state may be made exactly from by a process that succeeds with certainty.